Este blog reúne material del curso de posgrado "Análisis de redes sociales" dictado en la Universidad Nacional del Sur (Argentina).
lunes, 17 de junio de 2013
domingo, 16 de junio de 2013
sábado, 15 de junio de 2013
La geografía de los Tweets
The geography of Tweets
By Miguel Rios (@miguelrios), Visual Insights Manager - Fuente
Give every Twitter user a brush and they will paint you the world — if they geotag their Tweets.
Those of us on the Visual Insights team are obsessed with the patterns that emerge from aggregated Tweets over time. A continuing curiosity is about the geographical shapes that surface in geotagged Tweets. The images we’re sharing here use all of the geo-tagged Tweets since 2009 — billions of them. (Every dot is a Tweet, and the color is the Tweet count.)
I’m especially fond of this view of Europe, because it shows all the maritime traffic from different cities and countries.


Seeing the clarity of the regional images led me to work up images for cities, too. Here are three favorites: Istanbul, Tokyo and New York. I like these in particular because of their uniqueness in data quality, leavened by my own qualitative taste. I hope you enjoy them. You can see more cities on our Flickr page.
Istanbul: 

Tokyo:
 New York:
New York:
Topics:
jueves, 13 de junio de 2013
Como la Agencia Nacional de Seguridad mapea redes de terroristas
How The NSA Uses Social Network Analysis To Map Terrorist Networks
Ever since The Guardian reported that the National Security Agency (NSA) has been collecting the phone record metadata of millions of Americans, the cable talk circuit has been ablaze with pundits demanding answers to what should be obvious questions.
Who knew about the program to collect data? (Apparently, all three branches of government). Who else has been supplying data? (Just about everybody,according to the Washington Post). What is metadata? (It’s data about data).
The question that nobody seems to be asking is probably the most important one: What is the NSA doing with the data and why do they need so much of it? The answer is a relatively new field called social network analysis and, while it may make people uneasy, the benefits far outweigh the risks, so it is probably something we will just have to accept.
The New Science of Networks
The story of networks starts in 1736, long before the United States became a country, when Leonhard Euler set out to conquer a famous math problem concerning the Seven Bridges of Königsberg. To solve it, he created a new form of mathematics called graph theory, which concerned itself with links and nodes in a network.
In the 1950’s, interest renewed in Euler’s networks. First, Anatol Rapoport introduced the concept of triadic closure, which asserted that networks grow when people meet through a central friend that they both know. Later, Erdős and Rényi showed that as networks got bigger, communication among the people in the network got much more efficient.
In the 1970’s a sociologist named Mark Granovetter argued that we get most of our information not through close friends, but through weak ties and in the 1990’s Watts and Strogatz built on Granovetter’s work by showing that small clusters of people naturally organize themselves into far flung networks.
So by the late 1990’s, the small field of network analysis had built into a full fledged science and it was about to be applied to an increasingly important problem: Terrorist networks.
Mapping Terrorist Networks
Valdis Krebs of Orgnet is a network scientist who in 2002 published a widely praised paperon mapping terrorist networks and has since consulted with the Defense Department on methods and approaches of evaluating and dismantling terrorist organizations.
While he isn’t privy to classified information, he describes on his website how an entire network can be mapped using commercially available software by identifying two initial suspects:

It used to be that law enforcement officers would simply watch the two men closely, but in the era of global jihad, that’s much too slow to save lives. The two might be peripheral to the conspiracy and it could take years before you could connect them to the leadership of the network, if ever.

It used to be that law enforcement officers would simply watch the two men closely, but in the era of global jihad, that’s much too slow to save lives. The two might be peripheral to the conspiracy and it could take years before you could connect them to the leadership of the network, if ever.
Here’s where the data from Verizon and other companies comes in. If you can analyze communication records, you can move much more quickly. However, you don’t want to look at everyone the suspects talk to because you’ll end up with mostly incidental contacts, like friendly neighbors and delivery men.
But if you kept Rapoport’s concept of triadic closure in mind and had full access to communication records, you could look for contacts the two suspects have in common and start to build out a map of the conspiracy.
The next step would be to analyze the contacts of the suspects’ connections, again looking for closed triads within the existing network. As you progress from link to link, a fuller picture begins to form (click to enlarge).
Once you have the network mapped, you can begin to mathematically analyze it, which is how important insights can be gleaned even before wiretapping and surveillance warrants have been issued.
You can, for example, assess who is well integrated into the network by calculating who is most central; who has the widest reach by counting how many people in the network are within two connections from them and who in the network provides a crucial role as a bridge between otherwise unconnected people (as Mohamed Atta, the uppermost green node, does in the 9-11 network above).
The result is an almost uncannily accurate picture of the leadership, who can then be targeted to dismantle the network. (It has been estimated that the 9-11 network could have been broken up if just three central nodes had been taken out).
It should be clear by now why the government regards access to communication records as so crucial to national security. If the system had been in place in 2001, there is a high probability that the 9-11 network would have been broken up, saving thousands of lives and trillions of dollars.
It would be impractical, to say the least, to get court orders for each and every connection a suspect has, most of whom would not even be investigated. Without a full data set, the social network analysis could not be done and more intrusive, but less efficient methods, would need to be employed.
So whatever you might think of the program, it is most probably here to stay. What is perhaps of greater concern is that this type of analysis is not unique to antiterrorism, but is increasingly becoming a basic fact of commercial life.
Beyond the cell phone companies, social networks like Facebook, Google+ and Twitter can analyze the communications of hundreds of millions of people. Retail giants like Amazon, Walmart and Target are sifting through our purchases in order to predict our future behavior.
Wherever we go, our movements, faces and actions are being analyzed and, more often than not, it is not the government.
The truth is that there is a dark side to technology and our privacy is being breached every day by someone, somewhere. That’s just a fact of modern day life. It seems to me that if we’re willing to accept it from marketers who are trying to to sell us goods and services, we should be able to tolerate it from those who are trying to protect us.
- Greg
Note: Special thanks for Valdis Krebs of Orgnet for supplying the network maps, calculations and consultation for this post.
Digital Tonto
jueves, 6 de junio de 2013
Redes de curriculums
How to Tap Your LinkedIn Network for Your Next Opportunity
Lindsey Pollak, Blog Linkedin
A recruiter once told me that he always has two stacks of resumes on his desk: one super tall stack of resumes he receives unsolicited from the Internet and one very short stack of resumes that have been passed along from people he knows and trusts.
Not surprisingly, when this recruiter has a job to fill, he reaches for the smaller stack of referred applicants first. It’s simply more efficient and effective to check out candidates who come with a recommendation from a trusted friend or colleague.
So, how do you get your resume into the coveted short stack? Here are some tips:
1. Put people first.
Instead of starting your job search with job postings, start with the people you know. Where do they work? Where did they used to work? Who do they know? What advice and introductions can they provide?
The new LinkedIn Jobs makes this easy by showing you all of the companies (that are currently hiring) where you have LinkedIn connections. Just scroll down the main Jobs page to “Jobs in Your Network” and start browsing opportunities. You can also visit the LinkedIn Company Pages of the organizations on your prospect list and view anyone in your network who currently works or used to work there.
2. Gather information and build relationships.
Now it’s time to reach out. Before you apply for any position, try to speak with or have an email exchange with someone who has worked or currently works for the employer — in other words, conduct informational interviews. Your goal in these conversations is not to ask for a job or even to ask for your resume to be passed along. Not yet. Your objective at this point is to gather information that will help to: 1) give you an edge when you do apply for a position, and 2) build a relationship with the person providing the information so that in the future this person will make a referral.
Here is what you might say in an outreach email to an existing connection:
Hi Rachel,
I hope all is well – I loved the recent article you posted on LinkedIn about the new iPhone. As you may know, I am in the midst of a job search and I was wondering if you would be willing to provide a bit of guidance. I am very interested in a position in IT support at Nike and I know that you worked there for several years. Would you be open to a brief phone chat or to answer a few questions by email to provide some insight into how Nike hires and what they look for? I would be so grateful for your time and very happy to return the favor.
Thanks,
Lindsey
Here is what you might say in an outreach email to a friend-of-a-friend (second degree connection):
Hi Roger,
I hope all is well. As you may know, I am in the midst of a job search for a senior communications position and I’m in the process of researching potential employers. I saw on LinkedIn that you are connected to Joan Harris, who works for Red Hat, a company I deeply admire and would love to work for. Joan is very active on LinkedIn and posts great content about the company, so I’m hoping she might be open to a chat with a potential applicant. Would you be willing to make an introduction? I would be grateful for your help and of course happy to help you in any way I can.
Thanks,
Lindsey
You’ll want to send as many emails like this as possible to increase your chances of gathering good information. Notice how important it is to review each person’s LinkedIn profile before reaching out so you can customize your request and prepare yourself for any conversation the person agrees to.
When people do agree to speak with you, here are some questions you might ask current or former employees of your prospect companies:
- May I tell you a bit about my background [if you don’t know the person well] and why I think this position and company would be a good fit? (It’s important that the person knows about you and your goal so you can focus the conversation.)
- How did you land your position at the company?
- Would you share any tips about how to stand out in the application or hiring process? (For example, what to include/not include on my resume or LinkedIn profile, what to say in my cover letter, when and how to follow up)
- Would you be willing to review my resume or LinkedIn profile and provide any feedback? After I make any of your suggested changes, would you consider passing my information along to the recruiter or [if the person no longer works at the organization] to someone you know at the company who might be willing to pass it along?
- Is there anything I can do to help you?
If your contact agrees to refer you or your information to a recruiter, you will want to send an immediate thank you message. Then be sure to keep this person in the loop as your candidacy progresses by providing occasional updates on the process and, of course, another thank you note if you land the job.
If your contact is not willing to pass along your resume or LinkedIn profile, that might be a sign to you that 1) your credentials are not a good fit for the organization, 2) this person may not yet know you well enough to make a referral, or 3) this person is just not that helpful (hey – it happens). No matter the reason, go ahead and move on to other prospects.
3. Maintain your connections.
Since no single conversation or referral is guaranteed to lead to a job, you’ll need to continue this process of reaching out to contacts, asking for advice and keeping people posted on your progress. One great new way to keep all of your relationships active and strong is to use LinkedIn’s new Mentions feature.
Mentions makes it quick and easy to have brief conversations with the people in your network by allowing you to directly reference a contact in your LinkedIn status updates on the homepage. The person you mention will receive a real-time notification, which will keep you on his or her radar screen and promote ongoing discussion – which could lead to an opportunity.
You might use mentions to call attention to an article that would interest one of your recent informational interviewees, congratulate a connection on a new job or promote a company’s status update that celebrates an achievement by one of your connections.
The goal of using mentions in this situation is to keep in touch with your connections without being overly aggressive. And, as always, remember that the more you help and support people in your network, the more likely they are to want to help you in return. That’s what it means to tap the referral network.
martes, 4 de junio de 2013
Redes de deudores: el caso de Europa
Open Data y análisis de red: exposición a la deuda soberana de la UE
¿Se puede hacer algo con estos datos? Este es el desafío de cierre de todos los artículos en el Blog de datos Guardián , punto de referencia mundial para el periodismo de datos-conducido . Frase siempre acompañado de enlaces a los datos y metadatos descargables y reinterpretada por los lectores y Ddj aspirante.
El 26 de marzo, en relación con la crisis bancaria en Chipre, un mensaje por Simon Rogers titulado ¿Dónde están los bancos europeos más expuestos? ha puesto a disposición los resultados de una encuesta de la " Autorithy Bancaria Europea que muestra la exposición bruta al la deuda soberana de los países de la UE, con datos a nivel de país y de la institución.
Los datos , actualizados a finales de junio de 2012, el espectáculo que los bancos cuentan con € 3,6 billón de la deuda soberana y que los países tienen la mayor exposición.
Los datos son mapas navegables a través de un cuadro que le permite resaltar una nación específica, con una lista de los bancos que poseen su deuda.
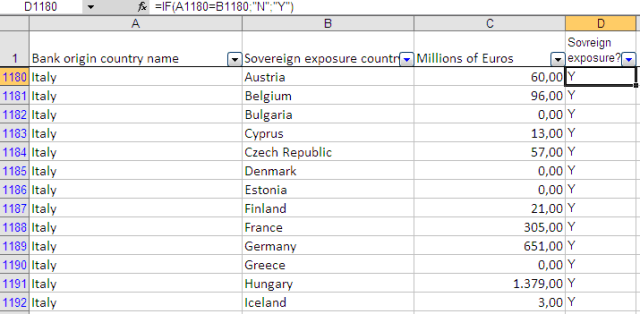
Por ejemplo, en el caso de Italia, la mayor parte de la deuda pública está en manos de los bancos nacionales, pero una parte importante está en manos de bancos extranjeros, y la misma situación, aunque con diferentes volúmenes se observa en otros países de la UE.
Lo que no surge directamente de este excelente durante la lectura de datos es el aspecto relacional . Por tanto, es interesante examinar las interdependencias entre las diversas naciones que entender que son más interconectado y mutuamente dependientes, a continuación, desde el punto de vista de la deuda soberana.
Veamos a continuación, tomamos el reto de Simon Rogers (se puede hacer algo con estos datos?) Y vamos a ayudarle a Red de Ciencia y sus métricas de herramientas relacionales necesarias son una simple hoja de cálculo y Gephi , para el análisis y mostrar.
Comenzamos a explorar y limpiar la hoja de cálculo original, eliminando las filas de subtotales y de cada país, la deuda soberana de propiedad de los bancos nacionales (por lo que en este análisis no consideramos que la deuda que mantiene "in-house").
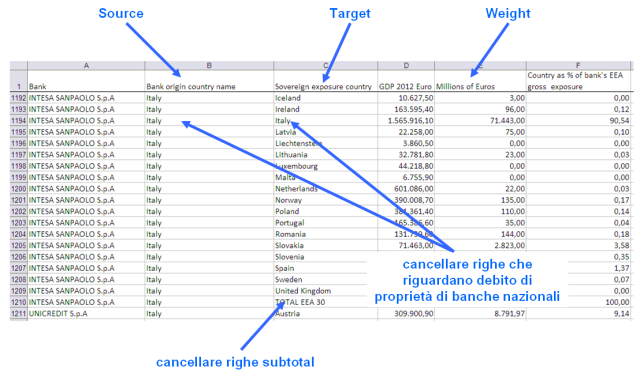 Para borrar el subtotal y las líneas con respecto a la deuda que se mantiene dentro de las fronteras nacionales pueden utilizar para campos de cálculo con una simple SI fórmulas :
Para borrar el subtotal y las líneas con respecto a la deuda que se mantiene dentro de las fronteras nacionales pueden utilizar para campos de cálculo con una simple SI fórmulas :
Así podemos crear dos tablas pivote obtener una lista de nodos y un borde de listaimportados en Gephi ( tabla de datos, hoja de cálculo de importación ).
La lista de nodos es, para todas las naciones, la parte de la deuda soberana de los bancos extranjeros. La lista de los bordes representa la división por países. Para más información, lea la hoja de cálculo adjunta .
En este punto, vamos a discutir el conjunto de datos desde una perspectiva diferente.
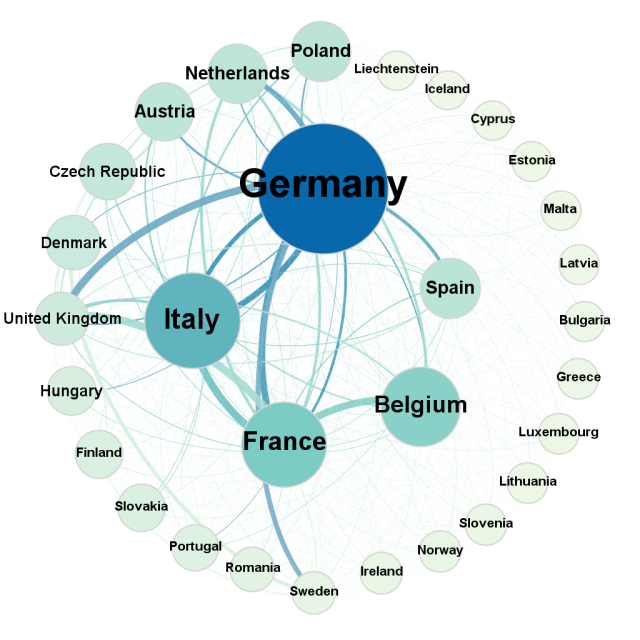 Una forma de representar a la agrupación de datos es un diseño con un círculo doble ( doble planta circular ), el círculo íntimo de los 5 países que tienen una mayor fragmentación de la deuda soberana en los círculos exteriores de las naciones restantes. El tamaño de los nodos es proporcional a la cantidad de la deuda y el color cambia a azul dall'azzuro acuerdo con la misma métrica.
Una forma de representar a la agrupación de datos es un diseño con un círculo doble ( doble planta circular ), el círculo íntimo de los 5 países que tienen una mayor fragmentación de la deuda soberana en los círculos exteriores de las naciones restantes. El tamaño de los nodos es proporcional a la cantidad de la deuda y el color cambia a azul dall'azzuro acuerdo con la misma métrica.
Deseo hacer hincapié en la interdependencia puede ser utilizado para los algoritmos de detección de la comunidad con el fin de entender lo que es el conjunto de las naciones, a continuación, los conjuntos de estados más interconectados y son interdependientes.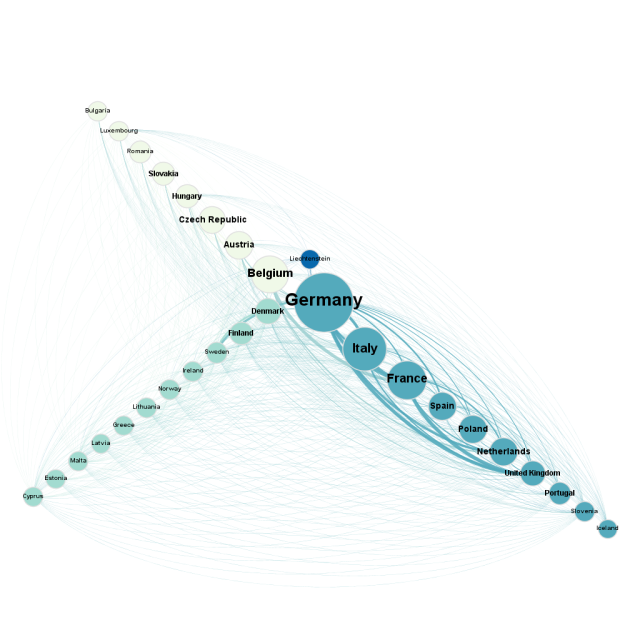 Una representación posible explota el potencial del diseño del eje radial . Los grupos fueron más fuertemente se distribuyen en 3 ejes y ordenados de acuerdo a la cantidad de la deuda soberana. El color de los nodos, en este caso, identifica la pertenencia a un grupo específico de estados. En la figura anterior se puede ver la situación particular de Liechtenstein, que se encuentra en el centro de los dos grupo liderado por Alemania y Bélgica.
Una representación posible explota el potencial del diseño del eje radial . Los grupos fueron más fuertemente se distribuyen en 3 ejes y ordenados de acuerdo a la cantidad de la deuda soberana. El color de los nodos, en este caso, identifica la pertenencia a un grupo específico de estados. En la figura anterior se puede ver la situación particular de Liechtenstein, que se encuentra en el centro de los dos grupo liderado por Alemania y Bélgica.
 Una representación posible explota el potencial del diseño del eje radial . Los grupos fueron más fuertemente se distribuyen en 3 ejes y ordenados de acuerdo a la cantidad de la deuda soberana. El color de los nodos, en este caso, identifica la pertenencia a un grupo específico de estados. En la figura anterior se puede ver la situación particular de Liechtenstein, que se encuentra en el centro de los dos grupo liderado por Alemania y Bélgica.
Una representación posible explota el potencial del diseño del eje radial . Los grupos fueron más fuertemente se distribuyen en 3 ejes y ordenados de acuerdo a la cantidad de la deuda soberana. El color de los nodos, en este caso, identifica la pertenencia a un grupo específico de estados. En la figura anterior se puede ver la situación particular de Liechtenstein, que se encuentra en el centro de los dos grupo liderado por Alemania y Bélgica.
Cierre el mensaje que indica que, al no ser un experto en finanzas internacionales, no son plenamente capaces de evaluar los méritos y si es una desventaja o una ventaja distribuir o concentrar su deuda soberana. Simplemente disfruté reelaborar una fuente autorizada con una perspectiva diferente. Cualquier comentario o sugerencia es apreciado y bienvenido.
Y tú, que haces algo con estos datos?
Créditos y recursos
Suscribirse a:
Comentarios (Atom)